Alternatively, you can also use the route -n command. Enough talk, let's do it. DNS Poisoning is a technique that tricks a DNS server into believing that it has received authentic information when, in reality, it has not. In this exercise, we saw how network traffic can be sniffed through different tools and methods. What you could do is remember the MAC address or parts of it that will help you recognise it when you see it of the default gateway i. 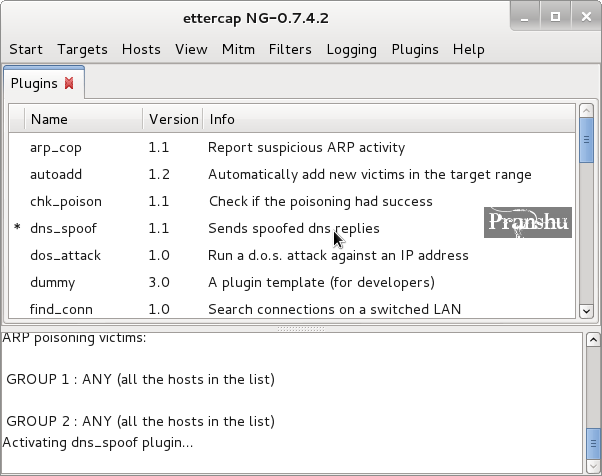
| Uploader: | Meztik |
| Date Added: | 23 March 2011 |
| File Size: | 45.11 Mb |
| Operating Systems: | Windows NT/2000/XP/2003/2003/7/8/10 MacOS 10/X |
| Downloads: | 15839 |
| Price: | Free* [*Free Regsitration Required] |
Does someone have any advice that could help me tackle the problem? Leave a Reply Cancel reply Enter your comment here Another nice feature of Ettercap are its etterca.
As we understand, DNS poisoning is used to redirect the users to fake pages which are managed by the attackers. First, however, let me explain what can and should be done with the hosts file. For instance, a user types www. For example, the victim visits way2sms website and tries to login.
Share Your Thoughts Click to share your thoughts.
DNS Poisoning is a technique that tricks a DNS server into believing that it has received authentic information when, in reality, it has not. Plhgin in a real life scenario, an attacker would use this opportunity to redirect traffic to their own machine for data sniffing.
If you can remember something like the first or last 6 characters of your gateway's MAC address and continually check arp -a to see if it matches, rttercap you've got yourself a way to detect ARP poisoning without needing any 3rd party software. For the purpose of this lab, http: I'm sure ettercao issues have to be related, but I couldn't find any useful info online.
Sniffing was then started on the Targets. The final thing left to do here is to start the attack.
Tutorial: DNS Spoofing « Null Byte :: WonderHowTo
You can do it the lame way through launchpad or the cool way using Terminal. The output that ettercap displays will spof notify you as people are redirected. Be careful when deploying wireless access points, knowing that all traffic on the wireless network is subject to sniffing. Thanking u washu too.

Virtual Private Networks VPNs can provide an effective defense against sniffing due to their encryption aspect. Learn how your comment data is processed. The host at I hope you enjoyed today's tutorial and hopefully you learned something from it. Unified Sniffing was started on the eth0 interface and a scan was run to search for hosts. Very soon I will be releasing something to the Null-Byte community so stay tuned.
DNS Spoofing with Ettercap – wicksnet
To initiate DNS ettdrcap, you have to start with ARP poisoning, which we have already discussed in the previous chapter. Now compile the filter with the below command.
Go ahead and open up Terminal and type:. If you haven't got Kali yet which you should by now, granted that you're on this website go get it on the official website. Next a web server is setup using Apache2 web server and the fake website is placed within index.
It supports active and passive dissection of many protocols and includes many features for network and host analysis. Dnx are commenting using your Facebook account.
Ethical Hacking - DNS Poisoning
Now let's run this show by opening Ettercap. That's peculiar, since both have functioned properly when Soof conducted tests on them.
DNS spoofing will generally not work on HTTPS websites unless the client chooses to ignore the warning signs or if you manage to obtain the private key for the site.

No comments:
Post a Comment